
EITIx
Security orchestration, automation and response solution.

Your All In One Solution!
EITIx SOAR is fully compatible with Wazuh, offering a sophisticated Security Orchestration, Automation, and Response (SOAR) solution seamlessly integrated with the Wazuh SIEM platform. This integration enables real-time threat intelligence sharing and centralized security operations, enhancing detection, investigation, and response capabilities.
EITIx promotes cross-departmental collaboration for efficient incident response and supports integration with a wide range of third-party technologies, ensuring a vendor-agnostic approach. By automating repetitive SOC tasks through customizable low-code workflows, EITIx significantly reduces operational overhead.
Leveraging AI-driven analytics, EITIx enhances threat detection accuracy, minimizes false positives, and supports scalability through version-controlled workflows and multi-instance deployment.
With intuitive drag-and-drop editors and configurable dashboards, EITIx provides a user-friendly yet powerful platform—ideal for organizations seeking a proactive, scalable, and comprehensive cybersecurity strategy built around Wazuh.
EITIx promotes cross-departmental collaboration for efficient incident response and supports integration with a wide range of third-party technologies, ensuring a vendor-agnostic approach. By automating repetitive SOC tasks through customizable low-code workflows, EITIx significantly reduces operational overhead.
Leveraging AI-driven analytics, EITIx enhances threat detection accuracy, minimizes false positives, and supports scalability through version-controlled workflows and multi-instance deployment.
With intuitive drag-and-drop editors and configurable dashboards, EITIx provides a user-friendly yet powerful platform—ideal for organizations seeking a proactive, scalable, and comprehensive cybersecurity strategy built around Wazuh.
EITIx Confidently Provide you:
Artificial Intelligence
Attack vector detection by AI.Security Alert
24/7 security detection and alertingMalicious IoC Detection
Alert on malicious file or website access.Vulnerability Management
CVE vulnerability live detection.Risk and Asset Monitoring
Cloud assets & organization risk monitor.Incident Management
Multi-phased ticket/case for incidents.Automated Custom Report
Customized and multiple audit reports.Proactive Threat Hunting
AI-driven detection of hidden threats before they cause harm.Why Choose EITIx Over Other Solutions?
1
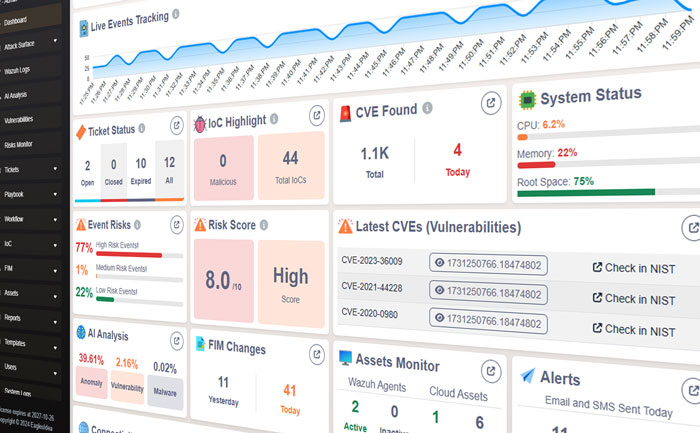
Everything in One Dashboard
Security team maintains multiple applications for multiple purposes. So, it becomes hard to login multiple apps daily to find security risks. But EITIx will provide all those features in a single application. This enables maintaining all the security operations in a single dashboard.
2
Threat Intel Automation
EITIx integrates the threat intelligence feeds such as MISP, NIST, VirusTotal, etc., to automate the malicious file, IP address, and website domain detection. So, the security team doesn’t need to scan IoCs in these threat intel feeds manually.
3
Artificial Intelligence (AI)
When you have millions of logs, it’s hard to tell if there are any phishing, malware, etc., logs. So, EITIx artificial intelligence (AI) enables users to view how many logs are related to which attack vectors. This also helps to identify threats that were not detected by your security detection rules.
EITIx is integrated with Wazuh SIEM. And EITIx users can analyze all the
logs in
EITIx. The main advantage is that EITIx provides you easy searching
capability
without using any complex query language like SQL.
Your organization may get millions of logs daily, making it hard to analyze
and
discover real threats. To solve this problem, EITIx provides a feature
called
‘Playbook’ where you can create custom rules to get only specific alerts.
EITIx artificial intelligence (AI) enables users to view how many logs are
related
to which attack vectors. This helps identify threats that were not detected
by
your own created security detection or threat hunting rules.
EITIx integrates the threat intelligence feeds like MISP, NIST, VirusTotal,
etc. to
automate the detection of malicious files, IP addresses, and website
domains. This
eliminates the need for manual IoC scanning by the security team.
EITIx enables monitoring of SIEM (Wazuh) agents' status, cloud, and network
assets.
This includes APIs, databases, and more, all within a single dashboard.
EITIx users can generate a security audit report quickly by scanning all the
agents
without manually summarizing data.
EITIx allows users to generate detailed audit reports by scanning specific
agents
without manual effort.
EITIx continuously scans agents and logs for potential CVE vulnerabilities
and
provides details on their risk severity.
EITIx has a built-in ticketing system to manage security incidents, assign
tasks,
add comments, and attach evidence.
EITIx scans files, IP addresses, and domains accessed by users, integrates
with
threat intelligence platforms, and alerts for malicious findings.
EITIx visualizes attack and threat events in real time on a world map for
easier
identification and analysis.
Transform Your Business with Expert IT Solutions
Contact us to get a quote and get started today with our expert IT services.